Flooding in computer science is a key method used to manage data flow in computer networks. This technique involves sending data packets to all connected nodes except the one where the packet originated. By doing so, it ensures that the information reaches its intended destinations, which can be especially helpful in dynamic network topologies.
When data packets arrive at a router, they are distributed through all outgoing links. This non-adaptive routing algorithm is crucial for quickly updating routing protocols and maintaining communication across various network devices.
Understanding how flooding works can help individuals appreciate the complexities of network communication and the role it plays in keeping information moving smoothly.
Flooding can also lead to challenges such as network congestion, which may slow down communication speeds. This aspect highlights the ongoing need for efficient routing algorithms that balance the flow of data packets while minimizing delays.
Understanding Flooding in Networking

Flooding is a common technique in networking that facilitates the distribution of data packets across a network. It can play a crucial role in routing and broadcasting messages.
By exploring its concept, types, and both advantages and limitations, one can gain a clearer picture of how flooding operates within network structures.
The Concept of Flooding
Flooding refers to a routing method where an incoming packet is forwarded to all outgoing links, except the one from which it was received. This technique ensures that the data packet reaches all reachable nodes in a network.
Flooding does not consider the shortest path; instead, every router sends the packet to each connected neighbor.
One common application is in broadcasting messages, like Address Resolution Protocol (ARP) requests. While flooding is effective in distributing data, it may lead to network congestion and efficiency issues. Uncontrolled flooding can cause broadcast storms, where excessive packets overwhelm network bandwidth.
Types of Flooding
There are different types of flooding techniques used in networking. The most notable are:
-
Uncontrolled Flooding: In this method, every incoming packet is sent to all outgoing links without any restrictions. This can lead to significant network congestion.
-
Controlled Flooding: This approach employs conditions to limit the number of outgoing links. For example, a router may send packets only to certain nodes based on network topology.
-
Selective Flooding: This method involves sending packets only to nodes that meet specific criteria, such as a sequence number. This helps mitigate the risk of network overload.
-
Sequence Number Controlled Flooding: In this variation, packets are assigned a sequence number to track their transmission, preventing redundancy.
These techniques vary in how they handle data traffic, making it essential to choose one that fits the network’s needs.
Advantages and Limitations
Flooding offers several advantages. It is robust, ensuring data reaches its destination even if some paths fail. This characteristic is beneficial in dynamic networks where topology changes frequently.
Additionally, flooding facilitates quick updates to routing protocols, allowing for fast communication between routers.
On the downside, flooding has limitations. Uncontrolled flooding can lead to network congestion and a broadcast storm, dramatically affecting performance. Security risks also arise as attackers can exploit flooding techniques to disrupt network operations.
Flooding-Related Network Protocols and Algorithms
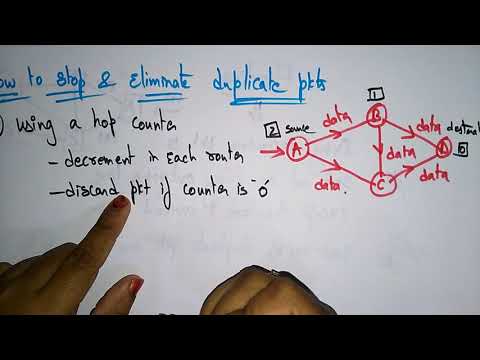
Flooding plays a significant role in various network protocols and algorithms. Understanding these protocols helps to manage data transmission effectively while addressing challenges like network congestion and efficiency.
Routing Protocols Involving Flooding
Several routing protocols incorporate flooding as a fundamental method for data transmission. One example is the Open Shortest Path First (OSPF) protocol, which utilizes flooding to share routing information quickly across large networks.
OSPF routers send updates to every node, ensuring all have the latest routing tables.
Reverse Path Forwarding (RPF) is another technique that enhances routing efficiency. It prevents loops by sending packets along the reverse path of the sender. These techniques, while effective, can increase network traffic and require adequate processing power to handle the data load.
Mitigating Flooding in Networks
Flooding may lead to network congestion and broadcast storms, resulting in decreased efficiency. To mitigate these issues, adaptive routing protocols are often employed.
These protocols adjust routing paths based on real-time network conditions, minimizing unnecessary packet replication.
Firewalls also play a critical role in controlling traffic flow. By managing the time to live (TTL) for packets, they can limit how far a packet travels within the network, preventing excess flooding. Additionally, methods such as multicasting can deliver messages to multiple recipients without burdening the network with excessive copies.
Practical Applications and Challenges
Flooding algorithms find applications in various scenarios, including multicast transmissions and large network management.
They are especially useful in situations where a quick distribution of information is essential, such as in denial of service (DoS) attack mitigation.
However, challenges arise from the need to balance bandwidth and network efficiency.
High traffic can lead to delays, impacting service quality. Therefore, careful planning and implementation of these protocols are critical.
Network switches and routers must be equipped to handle increased data flow while maintaining optimal performance.
